People are working from home like never before. For the most part, offices are...
Enjoy being secure with us.
We run vulnerability scans, conduct risk assessments, write policies, fix problems, assist with compliance, and harden your business’s information systems.
The Plan
Afterward, we continue monitoring and protecting your information systems.

WHY CHOOSE US
Our commitment is keeping you safe.
We stay up to date with security so you do not have to.
Seamless Configuration
Have your system, with the help of our experts, protect itself.
Secure Communications
Your information is encrypted at rest and in transit.
Always There
Emergencies are not planned. We are here when they happen.
WHAT WE OFFER
Security and Compliance
Achieve compliance by using proper security mechanisms.

Information Security as a Service

IT Solutions
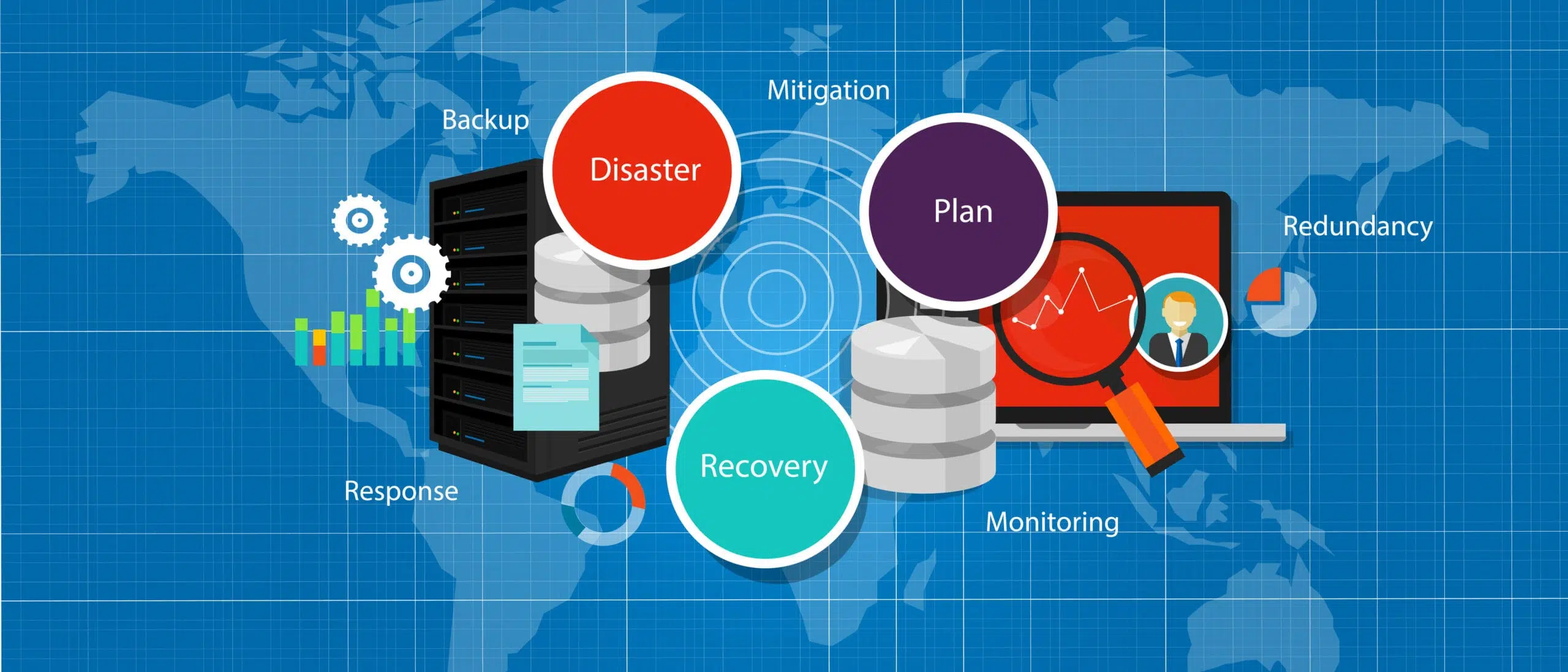
BDR Compliance

Data Security

Pen Testing

IT Governance Architecture
Cloud Protection
Cloud protection using directory services, MFA, encryption, hashing, etc.
Cyber Security as a Service
Real-world experience securing/protecting real-world environments
Compliance
Achieve compliance (HIPAA, PCI, CMMC, etc.) with our experts and partners.
Asset Protection
Cyber defense requires protecting physical assets as well.
IMPLEMENTING
industry-grade cyber security
Our security stacks are customized to protect organizations of all sizes. We use the best tools today to maintain business continuity while keeping companies secure and complaint.







Ready to Secure Your Business?
LATEST UPDATE
Learning
Removing Spyware From Your Phone
Before we can begin, if your Android is rooted or your iPhone is jailbroken,...
How safe is your ₿itcoin?
Whether one is investing, gambling, or collecting Bitcoin, one must secure it and ensure...
Business Email Compromise (BEC)
Business email compromise (BEC) is a type of cybercrime that targets businesses. In a...





